In this modern internet age, cyber crimes are reportedly increasing daily. You’ve probably got links in your inbox claiming you’ve won a prize or asking you to change your password! These are all different forms ofphishing attacksthat you should avoid.
No matter who sent this to you and how legitimate they appear, you should think twice before clicking on them. These suspicious links might trigger an automatic malware installation on your device, steal your data(which could be login credentials and banking information), or evenhack into your account.
The first-hand rule is toavoid the URL that you do not find trustworthy. However, there are different ways to determine whether the link is safe or fraudulent. Without further ado, let’s jump right into them.
Manual URL Inspection
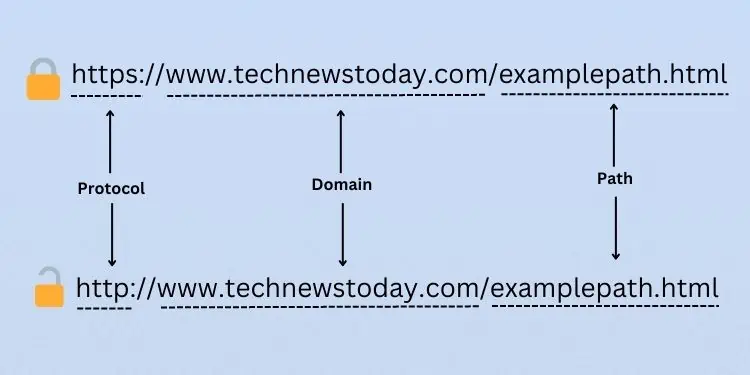
The most basic method to validate the link is through manual link/URL inspection. In technical terms, a URL can be broken down into several parts. For your simple understanding, these are the three basic components—protocol, domain, and path.
Let’s begin with Protocol. If alink contains ‘HTTP’ instead of ‘HTTPS’, it’s the first sign indicating the site is unsafe. HTTPS is the secured version of the former and incorporates SSL/TLS certificates that encrypt your information, thus adding an extra layer of security.
However, HTTPS isn’t the only thing to consider on a link. With improvements in technology, most attackers are already utilizing SSL certificates, making the links appear more authentic. In fact, some evenmimic the original domainto fool the users (URL spoofing). Others adopt this strategy to attack those netizens who may type the URL incorrectly (URL hijacking/typosquatting).
For example, a phisher might mimic the originalgoogle.comdomain asgoo-gle.com. Note that the two might look similar but the ‘-’ sign changes the context. This way, you can determine that the spoofed link is not safe.
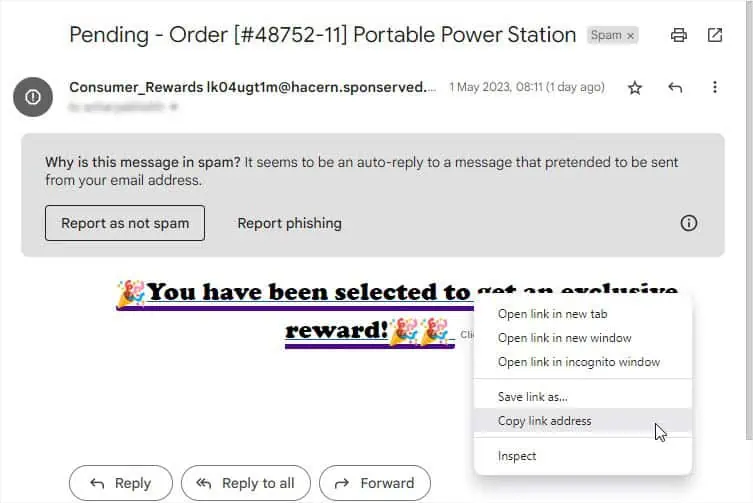
The third and most important part of an URL is the Path. you may easilyexamine the exact locationthe URL is trying to take you to. That’s the reason some attackers have started shortening the URLs using Bitly or similar tools. This helps hide the website’s file paths making it impossible to know whether it’s malicious. In such cases, manual inspection might not be the best option.
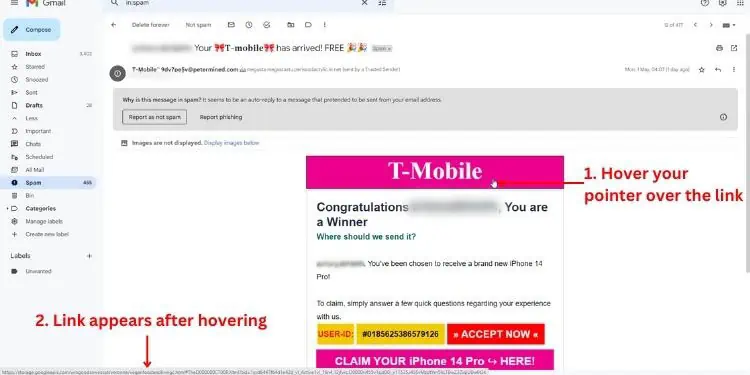
If you’re on a web browser, you might have noticed that different articles contain tons of linked phrases (and even images) directing you somewhere. To check the URL, you may simplyhover over the linked phrase,and you’ll likely get it from the bottom-left corner of the window.
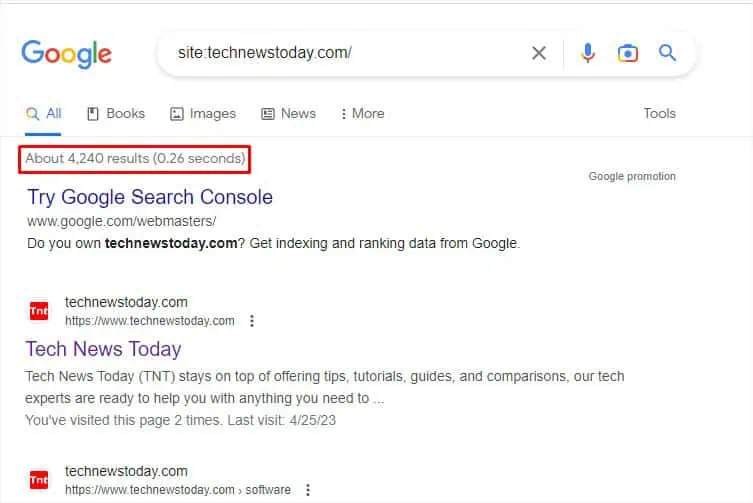
Using Site Operator in Search Engine
If you find the manual inspection method too difficult to understand, you do not need to scratch your head! It’s definitely not the only way to detect the link’s integrity.
One of the many methods is checking the search results on a preferable search engine. All you have to do is use the ‘site’ operator and enter the site’s name. If you get a large number of results, you can confirm that the link is probably safe.
Note:This technique might help validate the site but is not handy to get accurate results about a specified link/URL.
Use a URL Checker Tool
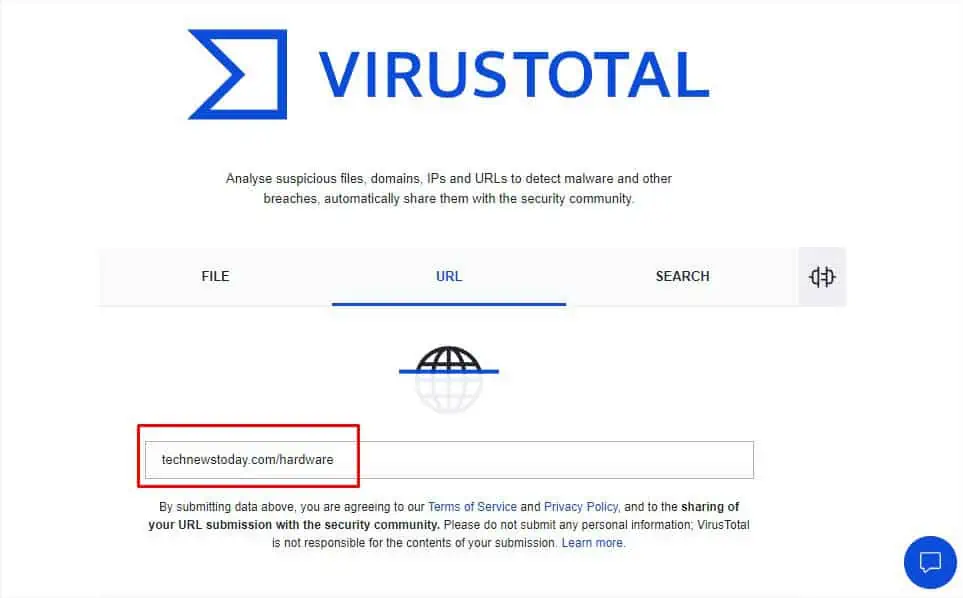
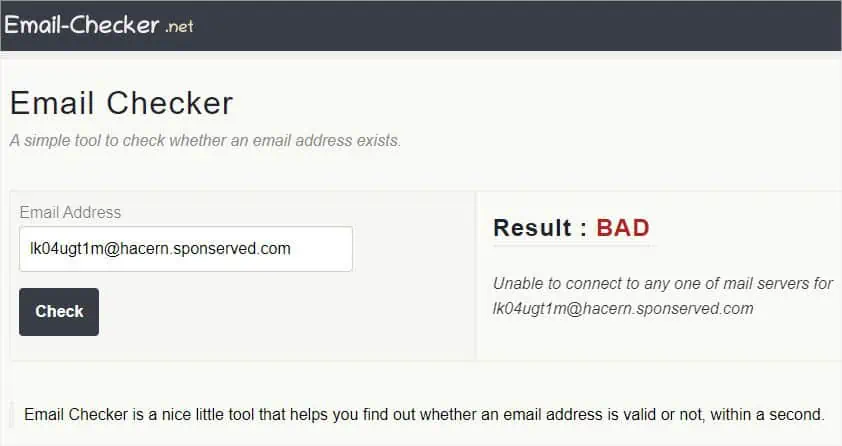
There are plenty of online URL-checking tools that let you test the provided link’s integrity. Some of these areGoogle’s Transparency Report, Virus Total, URLVoid, Scam Adviser,Norton’s Safe Web, and many more.
The interface of each of these tools might be different but the way they work is almost identical. They utilize various antivirus scanners and URL/domain blocklisting services to check whether the submitted URL contains any sort of malware or phishing components.
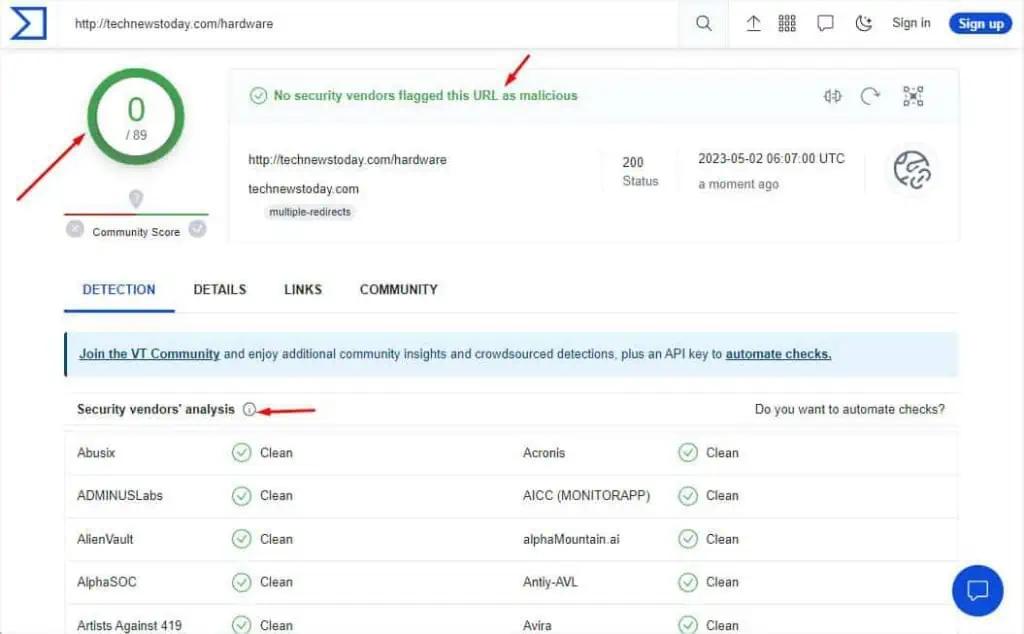
Additional Tip:Usually, all URL checker tools can display a site’s accurate analysis report. But if the URL is shortened, it might fail to show the details or provide inaccurate results. In that case, I suggest using aURL unshortener(available online) to get the final path and repeat the aforementioned steps.
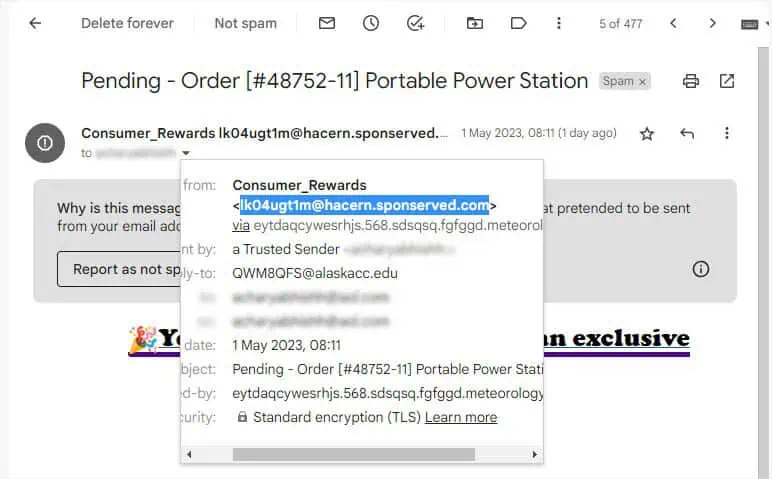
Verify the Sender’s Email Address
I’m pretty sure every one of us has received some form of phishing email that is too good to be true. You’re not the only one who wishes to validate this.
In the past, these suspicious electronic messages incorporated HTTP, and the URL was also easily differentiable. Upon my own research, I found out that attackers havestarted abusingstorage.googleapisto host malicious artifacts. Due to this reason, some malicious emails have bypassed the filtering process and landed in my Inbox instead of the Spam folder.
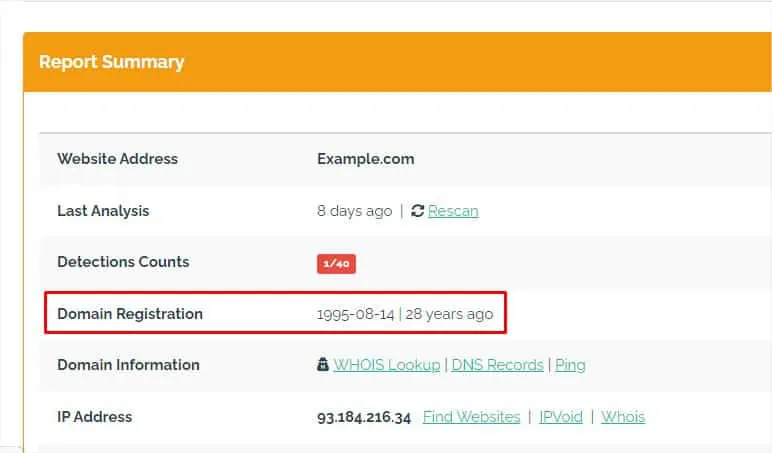
Although the link might appear to direct you to a trusted source, I wouldn’t advise clicking on it. You can check its integrity for yourself by validating the sender’s email address, and here’s how to do just that:
Test the Link in Virtual Machine or Sandbox
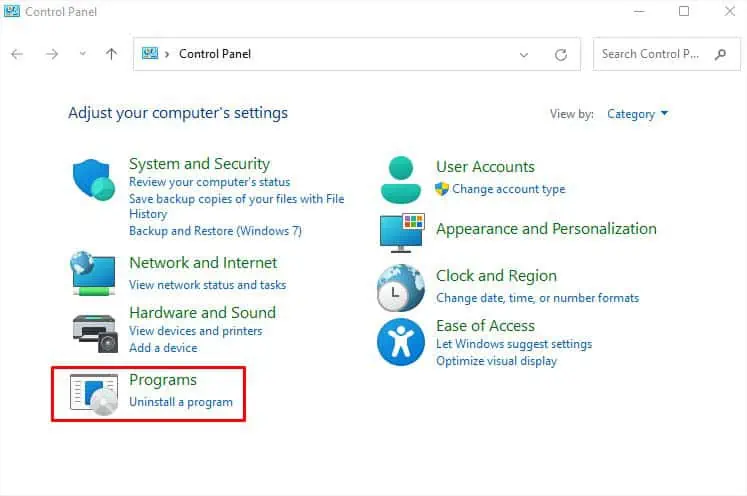
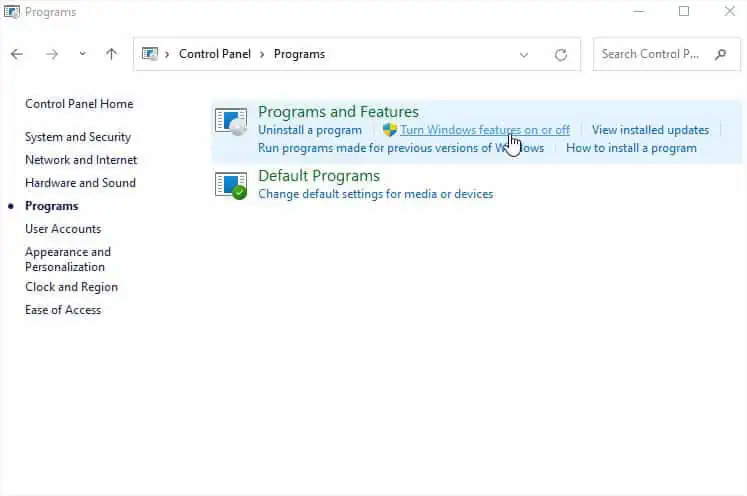
Virtual Machines and Sandboxes let you test the links without having to worry about your security (unless you share your private information). In fact, this is adopted by most professionals and would be the best option if you want to check out what the link could be dealing with.
While installing a virtual machine just to test a link would be a complex approach, you could instead utilize the built-in Windows Sandbox. But before that, make sure your PC meets the requirements. Then, follow the below instructions to quickly install the utility and visit the link to test its actual interface:
Utilize Browser Plugins and Mobile Applications
You can even opt for any third-party browser plugin/extension to verify all the links on a web page. All you have to do isadd the developer tool to your browserand simply activate them when required.
If you’re a Google Chrome user, you could pick Link Checker, WebGeekTools, etc. Likewise, Firefox users can opt for ScanURL, Dr. Web LinkChecker, etc.
Mobile users (both Android and iOS) can find a variety of applications on their PlayStore or AppStore. These free programs let you validate the SSL certificate’s validity and find possible malware/phishing components within the links.
What Should You Do if You Click on a Malicious Link?
If you have accidentally clicked on a malicious link, your personal data (login credentials and even bank details) is certainly at risk. Also, this could download some form of malware into your computer, or the attacker may erase/steal your valuable information.
However, you do not have to panic! Here are some things you need to avoid once you’re in the malicious site:
Once you ensure the aforementioned tips, you’re likely at less risk of getting infected. But some malicious links start working as soon as you click on them. Since this happens behind the scene, you won’t know what is happening.
If you notice unusual activities or have accidentally provided your information, here’s what you may do next: